Ransomware: Should You Pay to Get Back Seized Data? How to Avoid Having to Make That Decision in the First Place
Ransomware attacks are on the rise and pose a growing threat to us all. The cybercriminals behind them are electronically imprisoning computers and data belonging to government entities, healthcare institutions, law-enforcement organizations, private businesses, consumers, and more. No one and no sector is safe. Expect zero letup any time soon in the frequency and extent of ransomware attacks.
With all that in mind, BidPrime today is releasing the following explainer-animation, and soon a podcast, to give you not only a clearer picture of the problem but numerous tips as well to help you avoid becoming a ransomware victim (ransomware defense suggestions also appear later in this post, so please keep reading).
What is Ransomware?
Ransomware is any malicious software (malware) or virus that permits an intruder to access a computer and surreptitiously encrypt its stored data. From that point forward, the intruder has control of the system. The rightful owner is then blocked from using the computer and data until such time as a ransom is paid. Once you make the money drop, you receive untraceable keys and instructions to disable the ransomware.
(Chris Brunau with IT solutions provider Datto put together this comprehensive list that inventories and describes the various types of ransomware currently out there.)
The first known ransomware attack occurred in November 2013 with the unleashing of the CryptoLocker virus. Most early targets of ransomware attacks were state and local government agencies, with some historians identifying the Swansea (Massachusetts) Police Department as the first public sector victim.
Although ransomware plagues consumers, businesses, and governments alike (say it with me, “Nobody is immune to the threat of a ransomware attack”), we’re going to focus in this post on the problem as it relates to the public sector. Accordingly, in 2018, there were 53 reported ransomware incidents involving state and local governments. That compares to 38 such incidents reported in 2017.
The public sector annually spends many millions of dollars fighting ransomware and cleaning up the damage caused by attacks—millions more if you add in the price of the ransoms that get paid.
Most government agencies (and especially I.T. personnel) today consider ransomware to be one of the most consequential threats confronting the public sector. They understand that the stakes in this fight are sky-high. It doesn’t help matters that the bad guys’ modus operandi entails using ever-evolving, increasingly sophisticated tactics, or that implementing and enforcing the measures necessary to thwart ransomware attacks is a major challenge.
And not only are the attacks growing in number, they’re also becoming more brutal. In many ways, it’s like we’ve returned to the days of the Wild West, where bandits roamed freely and robbed banks or held up stagecoaches at will. In a very short time, we’ve gone from relatively modest attacks on entities such as the Swansea Police Department to hyper-aggressive shakedowns of the sort that recently occurred in Baltimore, Maryland.
They call Baltimore the Charm City. But there was nothing charming at all about the Robbinhood ransomware attack. It forced officials to shut down their servers citywide. Many Baltimore administrative employees were as a result prevented from performing their jobs (in desperation, more than a few resorted to conducting business the old-fashioned way—with pen and paper).
Here’s another one that caused severe disruption: SamSam ransomware. In March 2018, cybercriminals used SamSam to cripple government operations across the City of Atlanta. It cost that city nearly $2.5 million to undo the damage.
You’d think a smart ransomware attacker would only try to procure money from super-wealthy cities. That’s not the way these outlaws work. They opportunistically target cities large and small, located hither and yon, rich and poor. For example, they’ve hit Albany, New York; the San Francisco Municipal Transportation Agency; the Texas Department of Agriculture; Palm Beach, Florida, 911 services; the Port of San Diego, California; and the public school system in remote Forsyth, Montana (population, under 2,000). The list goes on and on.
U.S. State, Local, Federal Bid/RFP Activity
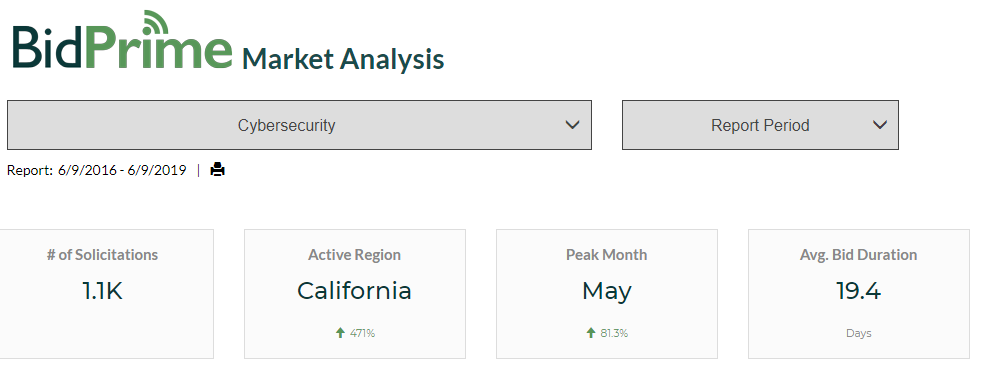
BidPrime over the past three years has seen a sharp increase in government bid/RFP activity for “cybersecurity” solutions and services. Indeed, these cybersecurity-related solicitations reached a high-water mark just this past May---a greater volume than observed in any other month over the past three years of this analysis.
Judging by the fast 19.4-day submission-to-award duration average of these cybersecurity solutions and services solicitations, it’s clear that many government entities are moving ransomware defense to the front burner. We’re also seeing state and local agencies—by a ratio of 3-to-1 over their federal counterparts—taking the lead on this (in our review of the last three years, December 2017 was the only month when the number of cybersecurity solutions and services solicitations originating from federal agencies outpaced those of state and local entities).
The most active U.S. regions for cybersecurity solutions and services solicitations are California, the District of Columbia, New York, Texas, and Maryland.
ACTIVE RELATED BIDS/RFPs
Cybersecurity
How to Avoid Becoming a Victim
The best way to avoid becoming a ransomware victim is to take precautions aimed at preventing that type of malware from ever finding its way into your computer systems.
To keep ransomware out requires two things: strong mechanisms and good policies, according to BidPrime Technology Officer Josh Schwartzbeck. “Your goal should be to make your policies and mechanisms so costly to breach that the attacker realizes your information isn’t worth the effort,” he explains.
No preventative measure is ever foolproof, Josh cautions. “Always assume that hackers will eventually find a hole, a way to get into your system,” he says. “This is why it’s also critical to install mechanisms for stopping attackers once they have found a way into your network. These post-penetration mechanisms can include but aren’t limited to tools like network access control, firewalls, encryption, environment separation, ‘need-to-know’ user permissions, and network and device scanning.”
Educate your staff. The first line of defense in the battle for information security isn’t computers but people. “The individual staffer is the point of greatest vulnerability,” says Josh. “That’s why data security has to be seen as a team effort.”
According to Symantec, most ransomware attacks are linked to employees failing to adopt effective protection practices. Therefore, you need to make sure your people know the score. Encourage them to err on the side of security by trusting their instincts. Train your employees to immediately contact the I.T. department if unsolicited or otherwise suspicious emails, links, phone calls, or other communications are received.
Never reveal personal data. Recognize that ransomware attackers are incredibly sneaky and persistent, and will use all means necessary to fool employees into dropping their guard. Emails and phone calls can be manipulated to appear legitimate and attackers often already have several pieces of information about the person they are attacking they can use to trick someone on the phone. The message you need to drill home over and over to your team is this: If something does not sound or look right, stop! Better to be safe than sorry.
And, speaking of being safe as opposed to being sorry, often remind your staff to update system passwords.
Give your IT department the resources it needs to address the threat. By resources, we’re not just talking about adequate funding. We’re also referring to leadership—and to the guidance that flows from it. Your I.T. team should employ the best in antivirus solutions and firewall defenses. They should as well copy the practices of prudent I.T. professionals, which means they should routinely filter and scan all emails and servers, and on a timely basis patch all systems and software.
Should You Pay the Ransom?
Once you fall prey to a ransomware attack, the obvious way to end the crisis is to pay the ransom. But should you? There are pros and cons to paying the ransom, and you should carefully weigh them all before deciding.
On the pro side, your system and data are restored to your control very soon after you pay. This helps you minimize the amount of harm spawned by an attack.
On the con side, paying the ransom can embolden the crooks to launch future attacks. Not necessarily against you again, but certainly against others who might not have been previously victimized. Plus, there’s no guarantee the system-nappers will free your data, since they have no incentive to do anything other than take the money and run.
Most state and local governments make it a policy to never accede to the demands of ransomware attackers. Only about 20 percent of government bodies feel it’s better to pay (by comparison, almost half of all other victims take that same course).
Over the years, we’ve contended that government entities—like all other organizations—need to have a solid disaster preparedness plan in place. Well, ransomware qualifies as a disaster and, consequently, should be addressed by a disaster plan. It deserves a section right alongside those covering things like backup solutions, generators, recovery systems, uninterruptible power supplies, continuity plans, backup software, and various elements of risk management.
“It’s surprising how many people don’t believe the computers and systems under their control are important enough to worry about whether they’ll become infected with ransomware,” says Josh. “They should worry about that, and for good reason.”
Count on BidPrime to Keep You Informed
You can count on BidPrime to continue studying this very important topic of ransomware. In addition, we’ll keep analyzing the public sector bid/RFP request and purchasing activity triggered by ransomware attacks or merely the threat thereof.
Do you want to know specifically what public sector agencies are requesting and purchasing in their fight against ransomware? For a BidPrime Market Analysis detailing the associated bid/RFP activity, contact a BidPrime representative at 888.808.5356 or email support@bidprime.com.
